


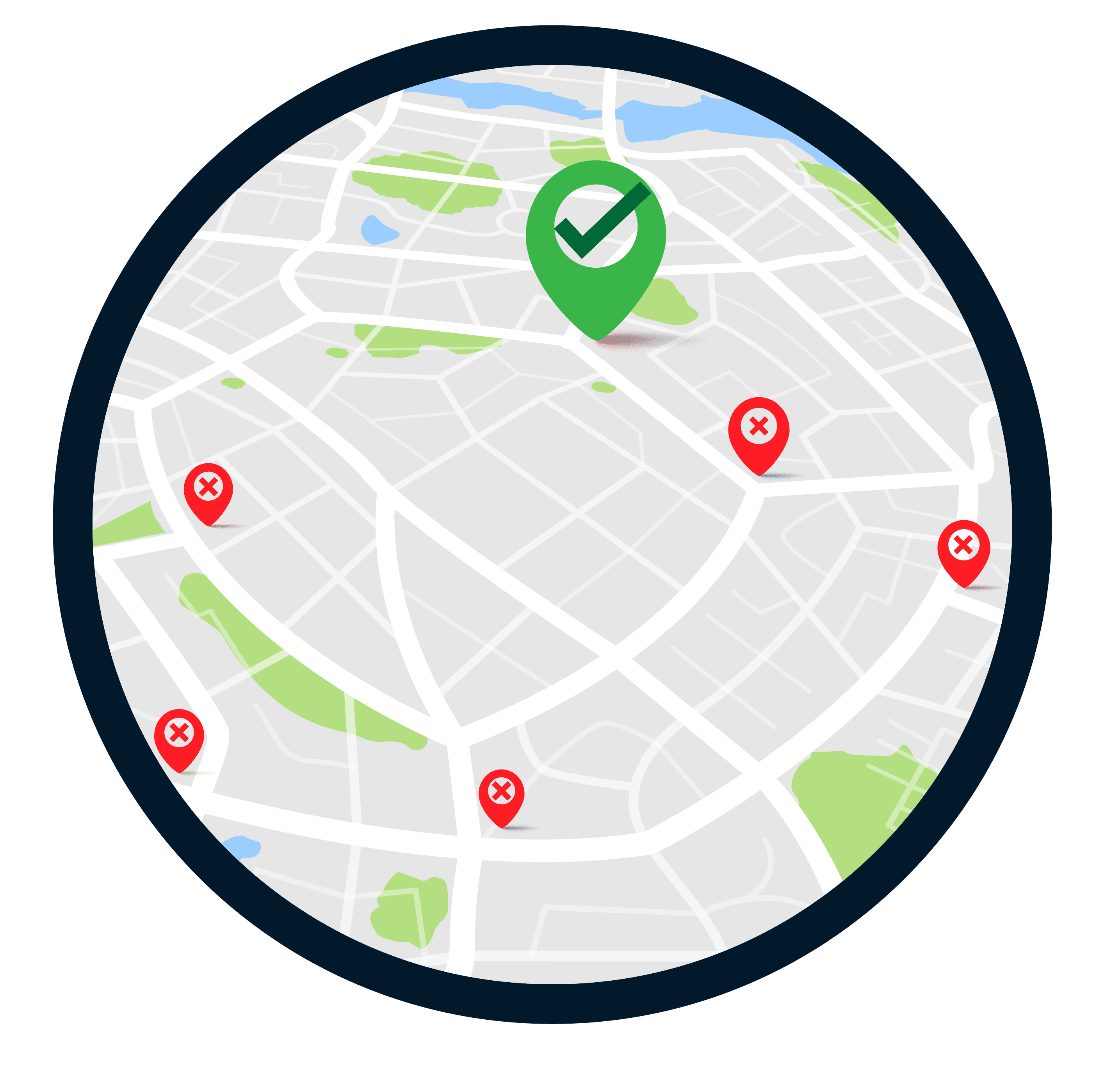
Geo-blocking is highly customizable and can be adapted for organizations based on their needs. If your team works in one central location, then geo-blocking can be enabled to only allow sign-ins from that location or even specific devices. For organizations with a hybrid or remote team, certain countries can be blocked to help fight against bad actors working outside the country.
Device-based rules can be implemented using
Microsoft Intune. Intune is a cloud-based endpoint management solution that is included in many of the Microsoft 365 subscriptions. It manages user access and simplifies app and device management including mobile, desktop and virtual devices. This can ensure that only approved devices that are managed by an organization can gain access to emails, files, or applications. Like other conditional access rules, these can be customized in a variety of ways to minimize disruption. For example, if users want access to email on their mobile device, that can be granted, but access to network files can be restricted to just company computers.
By putting conditions on how, what and where access to your resources can be achieved, you can reduce the ability of threat actor capabilities. To learn more about how this can be implemented within your organization, contact the CSOLVE team at salesdesk@csolve.ca.




The online silent auction returns as well opening on February 15th. Make sure to get your bids in on all the wonderful items available to show your support for this important cause in our community.
To learn more about the event, visit CLH Foundation’s site: A Red Carpet Evening | CLH Foundation


